In October 2024, the new SEMI E191 cybersecurity standard has been released in addition to the existing standards E187 and E188. While the previous two only give few hard instructions and can mainly be fulfilled by OEMs and fabs, SEMI E191 now gives software companies a clear opportunity to support machine manufacturers and fabs directly.
The current situation in the semiconductor industry
Production equipment in semiconductor fabs run in long-term operation for 20 to 25 years. It is safe to say that the machines life time largely exceeds OS innovation cycles. Tools today often operate with unsupported operating systems, meaning they are also no longer equipped with current security patches and thus pose a higher risk to malware threats. Although production floors are not connected to the internet, they are connected to other computers and host systems to enable further automation and optimized production flow. Closing this security gap is necessary.
The challenge is to get an overview of the current situation and obtain structured information on all existing computing devices in the factory with their operating systems, OS versions and security state information.
As soon as these data are collected, a reasonable risk assessment is possible and computing devices with security vulnerabilities can directly be addressed with updates and retrofits, ensuring uninterrupted production, prevent damages and be protected against IP and data theft.
Which Data to report?
The new SEMI E191 cybersecurity standard establishes a first stack of data that equipment suppliers shall provide for every computing device that is connected to the factory network and can be requested by the host at any time. Equipment suppliers are free to add further relevant data points.
| Operating System Information | Description |
|---|---|
| ComputingDeviceIdentifier | A unique value for computing device identification declared by the equipment supplier for the manufacturing equipment. Examples: computing device name, asset tag number, network hostname |
| OSManufacturer | States the operating system manufacturer name |
| OSName | States the operating system name |
| OSVersion | States the operating system version details (as declared by the OS manufacturer) |
| OSBuild | States the operating system build information - if not provided by the OS manufacturer, this shall be an empty string |
The subordinate standard SEMI E191.1, also released in October 2024, describes how to provide these cybersecurity data in accordance with SEMI E5 (SECS-II) using two new status variables.
„Computing Devices“ – Which IT components are meant?
Computing devices are defined as devices that can accept software modifications or execute software to perform an operation, as already stated in SEMI E188. They can be, for example, computers used to run the equipment control systems (ECS), analyses servers with an EDA interface as well as programmable logic controllers (PLC) or real-time operating systems incorporating high-performance sensors.
The standards explicitly excludes computing devices that are only connected to the equipment’s internal network or are provided by the fab, like MES (Manufacturing Execution Systems) or MCS (Material Control Systems).
According to SEMI E191, in some cases the computing device is not only required to state its own cybersecurity information, but shall be able to include further components, that normally do not need to align with this standard. They are not able to communicate their cybersecurity information directly to the factory network. In the example shown below it is a Recipe Server. The equipment supplier is responsible for ensuring that these data are correct and up to date.
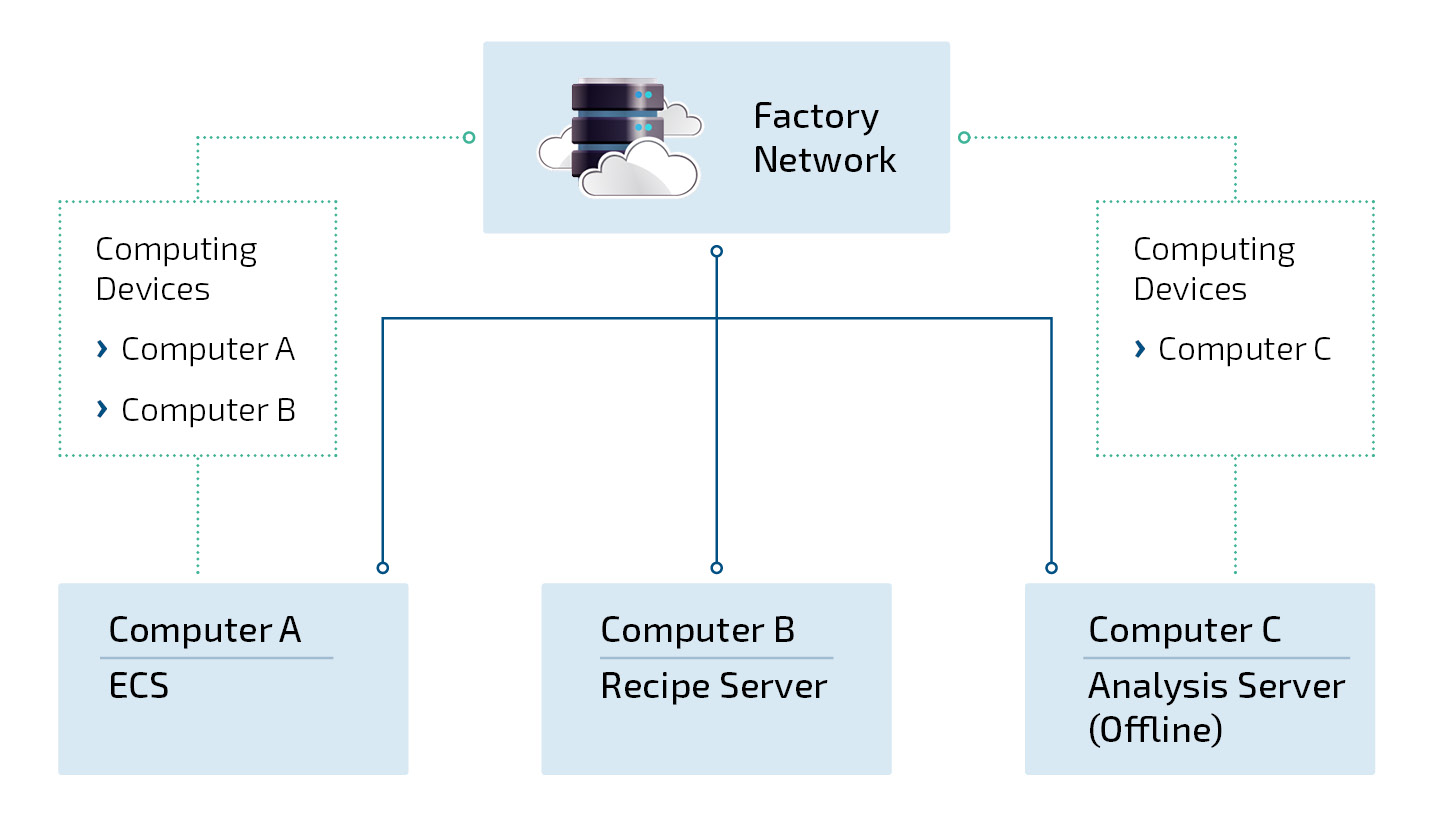
What’s up next?
Cybersecurity is an important topic that needs speedy tackling. SEMI E191 is a first and fast step into clearly defined action and utilized the well-known SECS-II communication already applied by a large number of OEMs. However, not all manufacturing equipment is equipped with a SEMI-compliant SECS/GEM, GEM300 or EDA interface. The CDS task force aims to find a way for those tools to provide these cybersecurity status information in a standardized manner as well. Furthermore they intend to add further cybersecurity status information referencing e.g., OS patches, service packs and components installed on the computing device. This will enable fabs to identify computing devices with security gaps that have already been closed, so they can concentrate on the computing devices that, in fact, are critical.
Would you like to find out more about the SEMI Standard E191 and how to prepare your equipment for it with the right software? Send us a message directly and we will get in touch with you as soon as possible.

