The Cyber Resilience Act (CRA) was passed by the European Union and came into force on December 10, 2024. Its implementation will present new challenges for many companies.
In parallel, the Semiconductor Manufacturing Cybersecurity Consortium (SMCC) has been formed as a new working group. Their goal is to interpret and harmonize national legislation for the semiconductor industry in order to define and implement uniform requirements worldwide. For us, this is the perfect opportunity to systems check our software for plant control and visualization: Where do we stand in terms of cybersecurity, the CRA and its implementation? We give you an insight into the security of our software and the ways in which we achieve this.
The Cyber Resilience Act (CRA): What is behind it and what is the timeline?
The Cyber Resilience Act is primarily aimed at manufacturers of products with software components, and also at their importers. The aim is to ensure cybersecurity throughout the entire product life cycle – from development through the life cycle to the end of the product’s useful life. Compliance is an important step in protecting products and customers from data and intellectual property theft, sabotage, and production downtime.
These are the important milestones of the CRA:
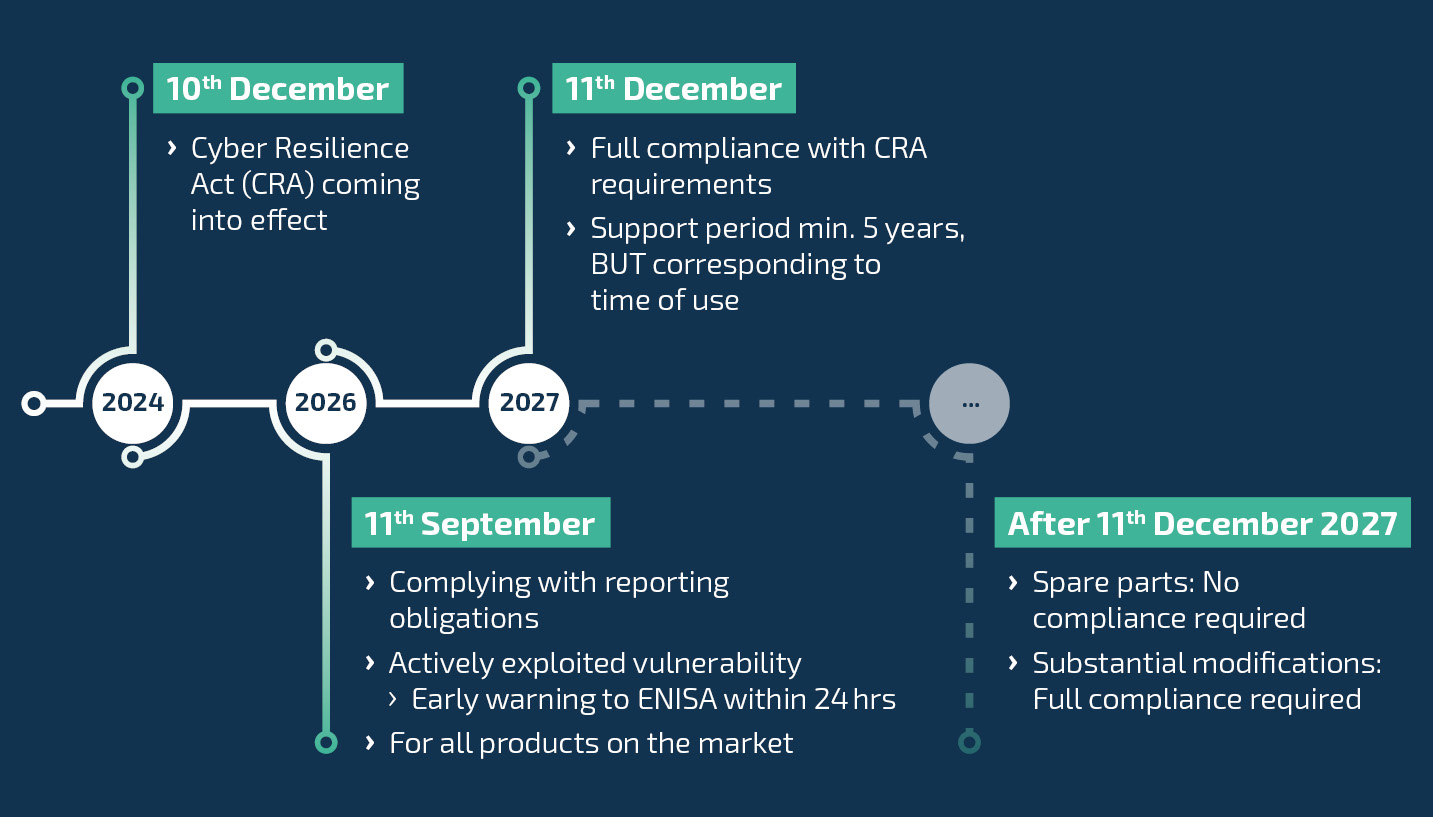
These clear milestones make cybersecurity a mandatory part of product development for all providers of products with digital components. Failure to comply with the CRA can have expensive consequences: Violations are punished with fines of up to EUR 15 million, or 2.5% of the company's annual revenue, whichever is higher.
Cybersecurity in our product development for the semiconductor industry – interview with Michael Arndt, our product owner
For us, cybersecurity is more than just a buzzword – it has been an integral part of our development processes for years. What is our current position with our software solutions for the semiconductor industry? I spoke about this with Michael Arndt, Product Owner for ToolCommander® – the framework for plant control systems – and FabLink®, the SEMI-compliant interface solution for plant integration in accordance with SECS/GEM, GEM300 and EDA.

Hello Michael! Cybersecurity has been a subject of our discussions for years. What does cybersecurity mean for you in product development?
Michael: That's right, cybersecurity is something we have been involved with for some time and is an integral part of the end-to-end development process. We consider security aspects as early as the design phase in order to identify and minimize potential risks and weaknesses at an early stage. All communication between systems and machines is encrypted to ensure data integrity and confidentiality. Access control mechanisms prevent unauthorized access and our processes meet current security standards. We also subject our architecture to regular audits and penetration tests. That is how we ensure that security loopholes are closed quickly.
And what do you pay attention to when choosing the tools you work with? Has anything changed there?
Michael: Security, reliability and compatibility with modern development standards are essential for us. The tools need to integrate seamlessly with our continuous integration/continuous delivery (CI/CD) pipeline and receive the latest security updates. The focus on open source software has increased, so we ensure that all libraries used are regularly checked and kept up to date. Compliance with industry-specific standards is also a decisive criterion.
You say that you identify and assess risks early on in order to consider safety aspects in product development. Where do you see dangers and weak points in semiconductor production that need to be averted?
Michael: Potential risks and weaknesses in semiconductor production lie primarily in the high level of connectivity and automation. Points of attack include, for example, unsecure interfaces, outdated software, and limited or inadequate access controls. The effects can be serious – from production outages to manipulation of process parameters to data loss or data theft. Attacks on sensitive intellectual property or process data are particularly critical, because they can seriously affect the entire supply chain.
Which security features did our ToolCommander® and FabLink® products have before cybersecurity became such a big hype topic?
Michael: Long before the current focus on cybersecurity, our products had security mechanisms such as
- Access controls: systems can only be accessed by authorized users,
- User role management: role-specific assignment of rights with assignment of individual accounts,
- Encrypted communication protocols: protection against eavesdropping and manipulation,
- Regular audits and penetration tests: continuous optimization of our security mechanisms
- Provision of SBOMs (Software Bill of Materials): transparency and traceability to identify potential vulnerabilities at an early stage
Testing designs for security risks was also a standard part of our development process from the very beginning. These foundations provide a sound basis for today's advanced cybersecurity requirements. Here, for example, we are working on tracking dependencies and evaluating Common Vulnerabilities and Exposures (CVEs) in order to prepare for the required reporting chains. We are also working on a customer portal which we want to use to provide software updates for our customers in the future. This will also allow us to reliably provide product maintenance and support.
By working with SMCC to implement CRA requirements, we gain further deep insights into the issues faced by OEMs and factory operators. Where do you see further potential to support them?
Michael: There are many ways to support machine manufacturers and fab operators in implementing holistic security concepts. This includes cybersecurity training, providing tools to continuously monitor the security situation, and integrating security updates into ongoing operations to minimize risks. By providing platforms and software products that reduce operators' workload, we can reduce complexity and increase security. In addition, we can provide analyses for network segmentation and attack detection to identify and ward off potential threats in good time. Another area of interest is providing assistance in complying with regulatory requirements, for example with security certificates and standardized audits.
Thank you for the exciting insight! If you would like to find out more about the products that Michael Arndt and his team are developing, you can find further information at ToolCommander® and FabLink®.
The Cyber Resilience Act (CRA) and its implementation in the semiconductor industry
The founding of the Semiconductor Manufacturing Cybersecurity Consortium (SMCC) underlines the importance and volatility of security along the entire supply chain and shows that cybersecurity is a common challenge.
The SEMI E187 and E188 cybersecurity standards were the first industry-specific guidelines created back in 2022, providing plant manufacturers and factory operators in the semiconductor industry with a framework and recommended courses of action. The SEMI E191 standard followed as a specific standard for software providers, which enables factory operators to obtain a faster overview of the security situation in the operating systems of all IT components involved in manufacturing. This allows targeted measures to be taken to close any gaps in security.
The role of SMCC in implementing the CRA, and striving for self-regulation in the semiconductor industry
The newly founded SMCC Working Group 8, which met for the first time in Brussels in February 2025, is working on implementing the Cyber Resilience Act specifically for the semiconductor industry. Due to the strong organization, extensive standardization and cybersecurity measures already in progress, the industry could be classified and recognized by the EU as a self-regulated sector. This would put the semiconductor industry in a similar position to the automotive and pharmaceutical industries, which do not have to comply with the CRA directly because they have their own stringent regulations.
The current SEMI standards are not yet sufficient for successful classification as a self-regulated industry. From our point of view, all companies working for the semiconductor industry should comply with the CRA requirements until more industry-specific standards have been created. These are expected – in a slightly modified form – to be part of upcoming SEMI standards.
Would you like to find out more about how we can make you fit for the CRA in the semiconductor industry? We will be happy to help you.
Your Contact Person



