Managers in the fields of IT, technical products, and R&D are facing increasingly complex management challenges as information technology (IT) and operational technology (OT) converge. Their systems and machines become more connected through integrated gateways, sensors, intelligent meters, communication devices, and routers, and they must address these issues:
- How do I ensure end-to-end encryption of the “talking” components?
- How do I maintaincontrol of the globally distributed device inventory during rollout, from commissioning to configuration and remote diagnostics?
- How can installation costs be reduced?
- How do I performautomatic maintenance, continuous analysis, and firmware updates proactively and as cost-neutrally as possible?
- How do I enable my “understaffed” and “overworked” IT team to detect connection or configuration errors quickly and efficiently and fix them remotely?
- How do I deal with the increasing heterogeneity of protocols, interfaces, applications, and operating and firmware versions of the device fleet?
The list of challenges could be continued at will and is certainly anything but complete. What these items have in common, however, is the question of how to guarantee modern and secure management of (IoT) devices.
Device management as a ready-made software tool in the IIoT environment can provide valuable support here if resources and time for in-house developments are in short supply. The following reasons serve to illustrate how this works:
Centralized and Proactive Device Management & Analysis
“Out of sight, out of mind” — this guiding principle has long been outdated in today's service & after-sales environment for mechanical engineering. Machines and systems are more connected than ever. Integrated sensor technology, controls, and gateways are essential components for ensuring the performance of the machines or continuously monitoring their “health”. Therefore, it is only logical to analyze the status of the (IoT) devices required for this in real time and to manage them centrally. Functional data such as CPU utilization, storage space, uptime, and connection status help IT managers proactively prevent overloads or outages. Since the devices are usually highly heterogeneous, IT and service & after sales can only keep track of everything if all the master data, device history, and installed software are continually maintained and documented digitally Direct assignment by user, location, or device type, as well as forming device groups, significantly speed up the administrative effort
Homogeneous Application Management With Docker Containers
When talking about common industry standards and protocols in IIoT, terms such as OPC-UA, MQTT, Ethernet IP, S7 communication, JSON, FINS, XML/HTML, or SQL databases are used, promising flexible data integration. In other words, homogeneous device management can be expected. However, the reality of machine manufacturers is quite different. There, it is not uncommon to find user-defined data models within one application protocol or even different firmware versions. If regular updates and changes are planned at application level, it makes more sense to manage them independently of the underlying operating system. The combination of different services on one device, with the aim of successively enabling them or enabling them at the user's request or of operating various machines in the machine park from one (IoT) device (e.g., device coupler), also makes managing applications more complex than less so.
Docker containers tip the scales here. Because it is in their nature — light, portable, and closed — to facilitate the development of different software and at the same time enable software updates, adjustments, and maintenance independently by loose coupling. This not only enables faster scaling, but also fallbacks to previous versions during tests in the agile development and rollout process. IT departments also benefit from tremendous portability when using Docker containers for their applications. Whether in a public cloud or firewall-protected environment. With an installed Docker environment, secure execution is possible.
Dealing with the Docker containers in which the applications run is part of the everyday work of IT experts. Device management, in turn, can provide valuable support for the homogeneous management of the containers. It offers the possibility to install multiple containers on individual devices, perform individual configurations, or carry out mass updates of entire device fleets or troubleshooting in a time-saving manner.

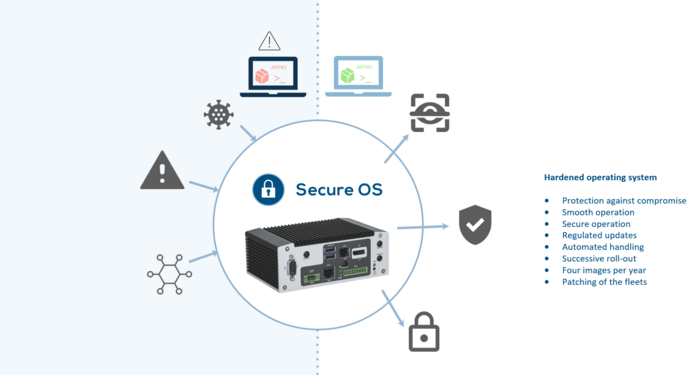
Securing (IoT) devices with hardened operating systems
For IoT devices to function smoothly, the firmware or operating system must be permanently kept up to date. Installed software always offers a certain gateway for hacker attacks. If there is insufficient bandwidth for regular updates, this creates additional uncertainty for IT managers, as 100% uptime cannot be guaranteed. To prevent this, it makes sense to reduce the operating system to its core functions, to completely deactivate unnecessary system functions, and set security functions so that no automatic updates are permitted at all. In this way, a secure or hardened operating system can be created, which is protected as much as possible against security gaps, while still allowing data transmission. In the event of critical vulnerabilities, the hardened operating system for X86 or ARM, based on Yocto Linux with full integration of device drivers, provides short-term updates, as it can draw on two redundant operating system partitions. In addition, it is suitable for placing the application on the operating system partition of a large number of devices with the same or a simple application and delivering both in one package. Since one to four update cycles per year are sufficient for such devices, this procedure is particularly suitable. Managing the application using containers, on the other hand, would be more than is necessary for this.
The secure operating system (Secure OS) contained in the device management thus provides a secure management interface for automatic availability, installation of updates, deployment, and rollback mechanisms.
Secure remote access to devices in the field
Whether the first version of a networked product is to be launched on the market, hundreds of devices have already been installed in the field, or old machinery is to be retrofitted with devices: When a service case is due or experiments are being conducted with new application functions (e.g., micro services), there is always a need for direct access to a dedicated device in the field. Medium-sized machine suppliers often lack the resources and expertise to support an industrial IoT system 24/7. This can be remedied by setting up diagnostics and automatic alerts in conjunction with a software-based remote maintenance service that enables timely troubleshooting. What IT managers therefore need is central management of remote access. Establishing the connection to the IoT device should be as convenient as possible, i.e., firewall-friendly without opening ports, and with one click. The connection can be established via a desktop or remote shell (graphical benchwork) such as RDP or SSH and terminated at any time. Security is paramount when setting up remote connections because it is precisely here that external points of attack exist that need to be secured. With system-based authentication mechanisms such as user-based rights management and an SSL-encrypted connection according to TLS 1.3 standard, IT managers can meet these requirements.

Increase service depth with VPN connections
Where remoting access to (IoT) devices is not enough, VPN connections enable temporary yet secure remote access to the machine and system network. A direct connection, also known as “tunneling”, is established between the networks of the machine manufacturer and the end customer by initiating it from a cloud service via a local VPN client. The user receives immediate feedback on the connection status (available, connected, disrupted).
Once the VPN connection with the (IoT) device has been successfully established, extensive remote maintenance such as parameterization, configurations on the machine control, live tests for firmware, and software installations can be performed by the machine manufacturer or system integrator.
Simultaneous connections are essential so that cross-functional teams can independently access a system or even several systems that are connected via an (IoT) device and provide remote support without delay. Detailed connection protocols that record duration, users, and transmitted data are indispensable to meet the obligation to provide proof and create transparency towards the end customer. Sophisticated user management and automatic deactivation of the connection after an hour of inactivity provide additional security.
In this way, system integrators and machine manufacturers can significantly increase their service depth and reduce their IT team’s VPN configuration workload.
User-friendly onboarding
The delivery of a system or machine always includes the networked (IoT) devices. To implement services such as remoting, container management, or real-time analyses, suitable software must be installed on the IoT devices on the one hand and connected to a specific cloud instance on the other, so that it is possible to control the device inventory from the cloud. The registration and unique identification of the device (name of the device, ID, REST coupling, etc.) takes place as part of the in-house commissioning process of the system when the software is installed. If systems in the field are subsequently equipped with IoT devices, this process can also be carried out manually via a mobile app. To obtain login authorization for device management, the user or service technician need only scan the QR code on the device and register. This onboarding process thus also enables easy assignment to the respective instance/system in the cloud. This allows technical product managers and IT managers to ensure that the IoT devices are up to date and equipped with the necessary services, both before delivery to the user and when retrofitting the machines.
Well-thought-out device management can support the IT of a medium-sized machine manufacturer or system integrator with managing their networked devices in many ways. Security concerns or administrative workload can be successfully addressed thanks to the user-friendly device onboarding, proactive monitoring, and a clear management interface as well as homogeneous and high-performance application and firmware management. In consultation with their IT, companies enable their service and after sales to set up digital services professionally and scalable.
